It keeps your CISO up at night. AI is making it easy for criminals to appear legitimate, they'll look perfect on paper and give great answers. But it's all fake.
Run 𝒳Chk in a browser window during your interviews and get real time alerts.
The Telegram channel for the Haotian AI face changing software announced a major update to the software about twelve hours ago. This technology is very popular with transnational organized crime groups doing romance scam attacks. In my travels researching AI face changing technology used for evil, this appears to be the top of the line of all of the options out there.
⚡️Integrated Face and Voice Replacement, truly achieving perfect synchronization of face and voice replacement packaging
⚡️Full Dynamic Facial Feature Bone Drive, a first in history! Precise micro-expression capture, blinking, lip licking, head shaking, fast head shaking, facial movement trajectory 99.8% naturally restored
Eric Huber - LinkedIn

Excellent report out of OKTA about the North Korean fake worker threat.
"While the primary objective of the ITW scheme remains financial gain through the payment of wages, there are numerous reports surfacing of data theft and extortion attempts against organizations that have unknowingly employed and later moved to terminate these workers."

Mass industrialization of deception: in this exclusive report, our Threat Intelligence team investigated Haotian AI, a company offering face-modification software via Telegram forming full-fledged enterprises dedicated to large-scale fraud and identity theft.
Haotian AI offers easy-to-use, customizable deepfake software capable of real-time face swaps with disturbingly high quality.
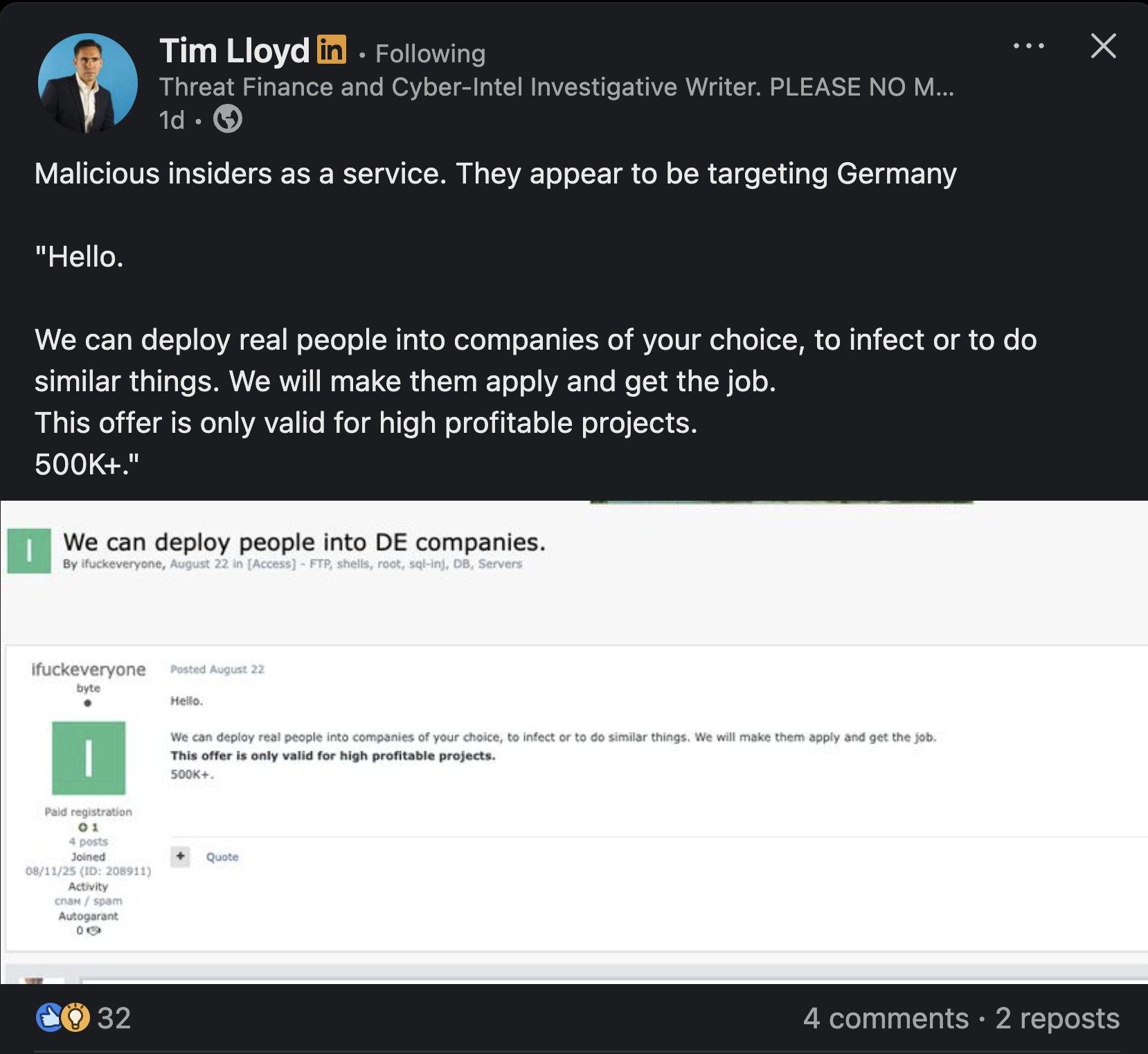
Malicious insiders as a service. They appear to be targeting Germany. "Hello. We can deploy real people into companies of your choice, to infect or to do similar things. We will make them apply and get the job. This offer is only valid for high profitable projects. 500K+."
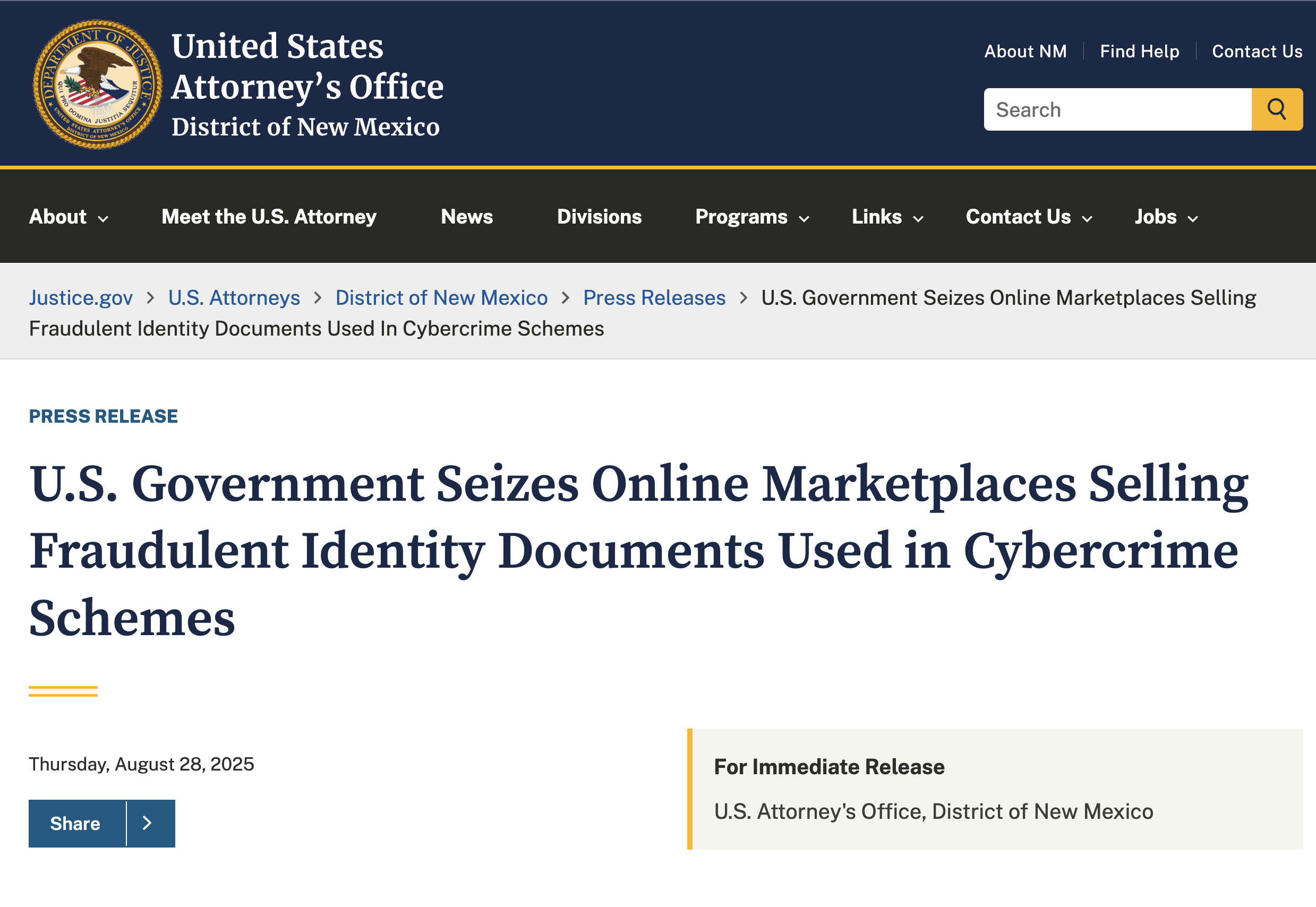
The U.S. Attorney's Office for the District of New Mexico announced today the seizure of two marketplace domains and one blog used to sell fraudulent identity documents to cybercriminals worldwide. The operators of VerifTools produced and sold counterfeit driver's licenses, passports, and other identification documents that could be used to bypass identity verification systems and gain unauthorized access to online accounts.
Nearly every Fortune 500 company is hiding the same uncomfortable secret: they have hired a North Korean IT worker. Despite how widespread the issue is, few companies are willing to talk publicly about it. Experts say reputational risk, legal uncertainty, and embarrassment all contribute to the silence — which in turn makes the problem harder to solve.
"It's moved beyond adolescent pranks and hacktivism," Moles told The Register. "It's moved beyond just ransomware guys trying to extort organizations. The skills and the techniques used by the nation-state actors have propagated right across the criminal enterprise. They're clearly all collaborating on various different underground forums and selling techniques and capabilities and services to each other. And it's not going away." ®
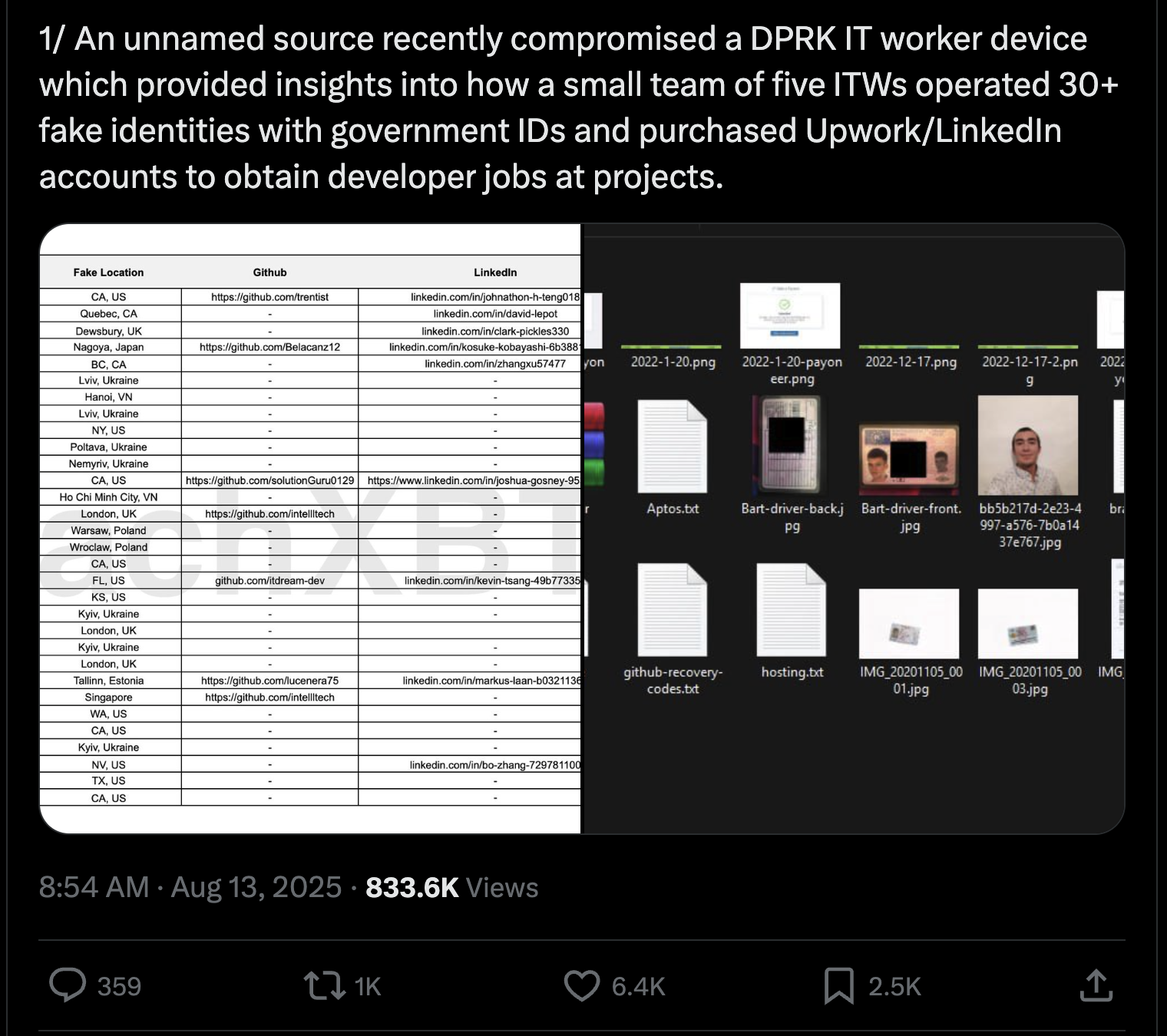
1/ An unnamed source recently compromised a DPRK IT worker device which provided insights into how a small team of five ITWs operated 30+ fake identities with government IDs and purchased Upwork/LinkedIn accounts to obtain developer jobs at projects.
Virtual interviews have become the new normal in hiring in recent years, driven by the rise of remote work and companies' desire to speed up hiring. Trouble is, more candidates are using AI tools to cheat by feeding them answers off screen, especially in technical interviews, recruiters say. In rarer cases, AI-enabled scammers are impersonating job seekers with the aim of stealing data or money once they are hired.
In this campaign, threat actors contact employees by text or phone pretending to be from human resources or IT. Their goal is to trick employees into giving up account access or their personal information.
But the issue isn’t confined to the tech industry. More than 300 U.S. firms inadvertently hired impostors with ties to North Korea for IT work, including a major national television network, a defense manufacturer, an automaker, and other Fortune 500 companies, the Justice Department alleged in May.
“Almost every CISO of a Fortune 500 company that I've spoken to — I'll just characterize as dozens that I've spoken to — have admitted that they had a North Korean IT worker problem,” said Mandiant Consulting CTO Charles Carmakal during a threat-intel roundtable, admitting that even Mandiant's parent company Google is not immune.